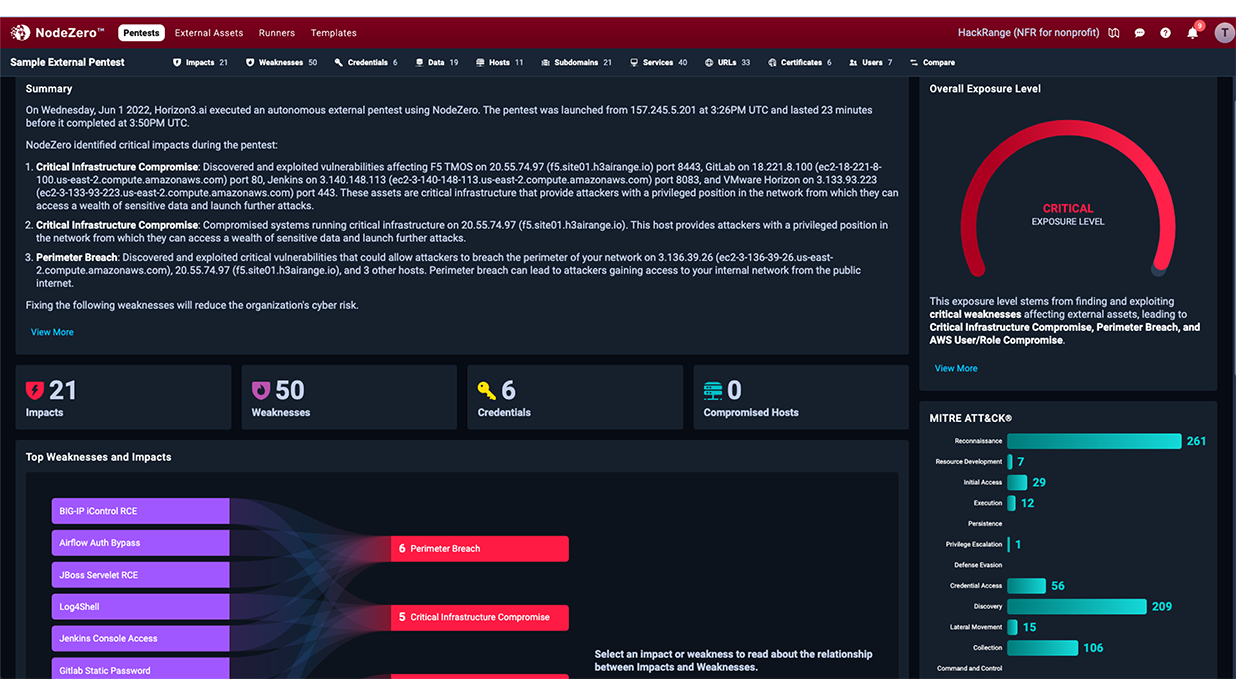
Continuous Threat Exposure Management (CTEM) promotes a proactive, continuous approach to identifying, assessing, and minimizing vulnerabilities within an organization's attack surface. Today, Autonomous Penetration Testing plays a key role in discovering exposed assets, such as servers, endpoints, cloud services, and applications, that attackers can exploit. It also identifies weaknesses that go beyond known and patchable software vulnerabilities, such as easily compromised credentials, exposed data, misconfigurations, poor security controls, and weak policies.
Importance of Continuous Threat Exposure Management
The significance of a CTEM program lies in its proactive approach to security. In the ever-evolving landscape of cyber threats, merely reacting to incidents is insufficient. Organizations must continuously assess their environments to identify vulnerabilities and weaknesses in their digital infrastructure that could result in a potential breaches. By understanding and managing their attack surface, organizations can prioritize security enhancements, reduce risk exposure, and safeguard critical data against unauthorized access.
Continuous Cyber Risk Assessment
Continuous assessment is a critical component of managing an organization’s attack surface. It involves regularly scanning and monitoring the infrastructure to detect new vulnerabilities and weaknesses as they emerge. This ongoing process helps organizations stay ahead of attackers by ensuring that any potential entry points are identified and addressed promptly. Technologies that facilitate continuous assessment are essential in building a resilient security posture.
The Role Of Remediation in CTEM and Attack Surface Management (ASM)
Once vulnerabilities are identified, the next crucial step is remediation. This involves fixing the flaws to mitigate risks and prevent exploitation. Effective technology from companies such as Horizon3.ai can provide risk prioritization, actionable insights, and recommendations for remediation, allowing IT security teams to address the most critical vulnerabilities first. Timely remediation is vital to maintaining the integrity and security of an organization’s IT infrastructure.
Verification of Security Measures
Verification is an essential follow-up to remediation. It involves confirming that fixes have been successfully implemented and that they effectively eliminate the risk of exploitation. Verification processes ensure that remediation efforts are thorough and that no residual risks remain. This step is crucial for closing the loop in CTEM and ASM and ensuring that the security measures in place are both effective and comprehensive.
Horizon3.ai
Horizon3.ai is a company that specializes in providing solutions for continously finding, fixing and validating exploitable attack surface. Their offerings include advanced scanning tools that help organizations discover vulnerabilities across their networks, including both on-premise and cloud environments. Horizon3.ai’s tools are designed to simulate real-world attacks, allowing companies to see how their defenses would stand up to an actual cyber threat.
NodeZero by Horizon3.ai™
NodeZero is an autonomous penetration testing solution from Horizon3.ai that safely exploits vulnerabilities and weaknesses in organizations’ infrastructures to show how an attacker could breach an environment. This proactive approach not only identifies vulnerabilities and weaknesses but also tests the effectiveness of the current security measures and incident response capabilities. NodeZero provides detailed reports that guide remediation efforts, helping ensure that vulnerabilities are properly addressed.
At HackRange, you as a student will be able to uncover the powerful capabilities of Horizon3!