Splunk
Splunk is a powerful platform designed for searching, monitoring, and analyzing machine-generated data in real-time. It is widely used in various industries, including cybersecurity, to gain insights from large volumes of data. Splunk collects and indexes data from various sources, such as logs, metrics, and events, making it easier to search, analyze, and visualize this data through its user-friendly interface.
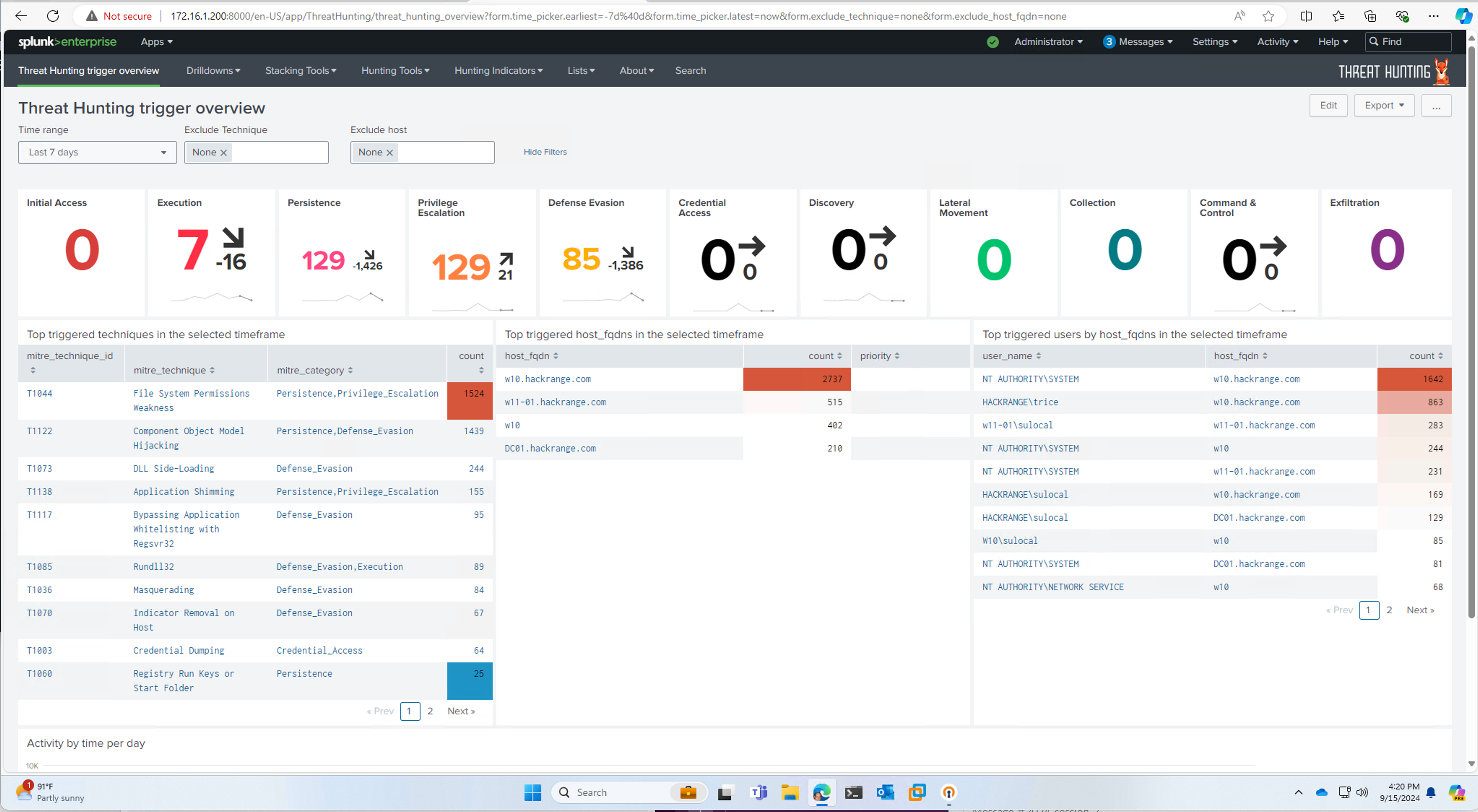
In the realm of cybersecurity, Splunk plays a crucial role by providing comprehensive visibility into an organization’s IT environment. It helps security teams detect, investigate, and respond to threats more effectively. By aggregating data from firewalls, intrusion detection systems, antivirus software, and other security tools, Splunk enables the correlation of events across different sources. This correlation is essential for identifying patterns and anomalies that may indicate a security incident.
One of the key features of Splunk in cybersecurity is its ability to perform real-time threat detection. Splunk’s advanced analytics and machine learning capabilities allow it to identify suspicious activities and potential threats as they occur. Security teams can set up alerts and automated responses to mitigate risks promptly. For example, if Splunk detects an unusual login attempt from an unfamiliar location, it can trigger an alert and initiate a predefined response, such as blocking the IP address or requiring additional authentication.
Splunk also excels in incident investigation and forensics. When a security incident occurs, Splunk’s powerful search capabilities enable analysts to quickly sift through vast amounts of data to trace the origin and impact of the breach. By providing a detailed timeline of events, Splunk helps security teams understand how the attack unfolded and what systems were affected. This information is critical for containing the breach, preventing further damage, and implementing measures to avoid future incidents.
Furthermore, Splunk’s reporting and dashboard features are invaluable for compliance and auditing purposes. Organizations can create customized reports and visualizations to demonstrate compliance with regulatory requirements and internal security policies. These reports can be used to provide evidence during audits and to communicate the organization’s security posture to stakeholders. Splunk’s ability to generate real-time and historical data insights ensures that organizations can maintain a proactive and informed approach to cybersecurity.
Here at Hack Range, our students will have access to Splunk and will configure endpoints that will send telemetry to Splunk.